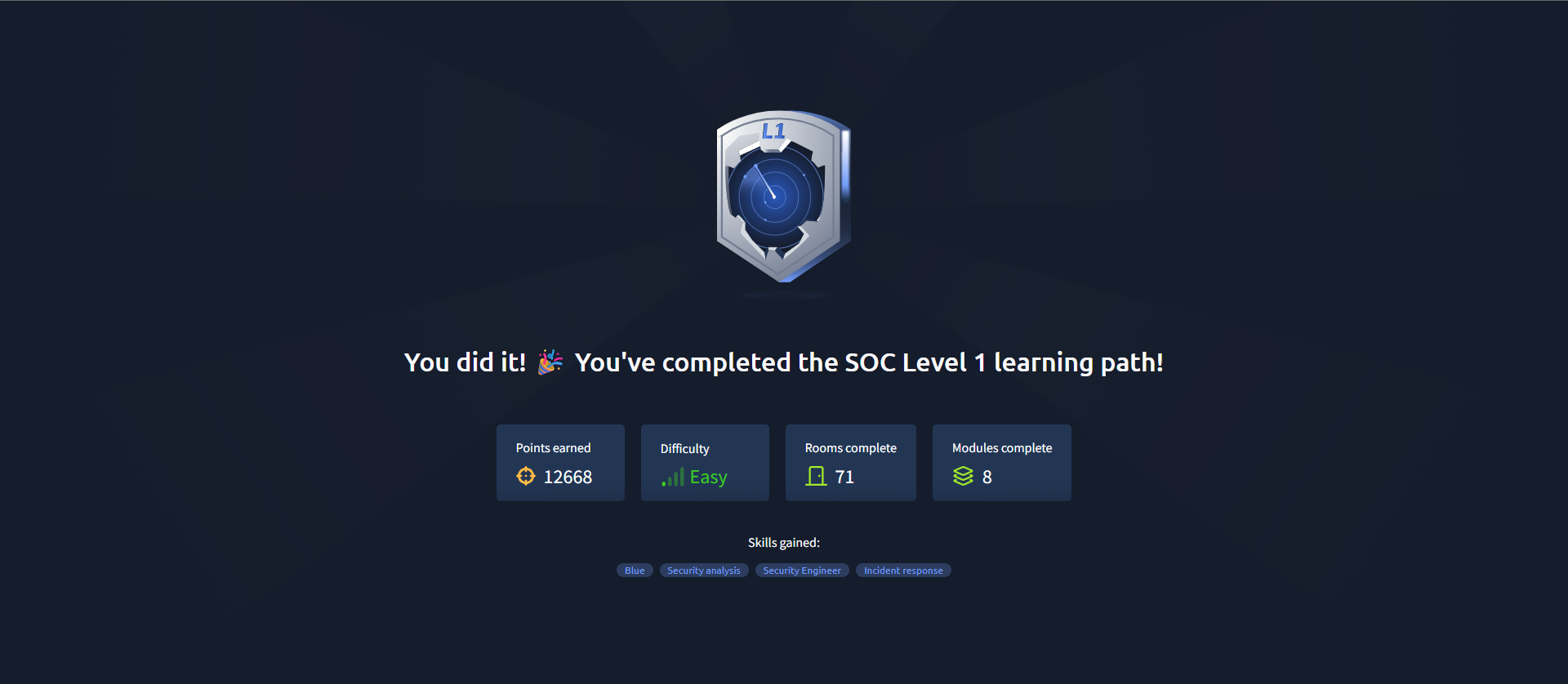
I finally completed the TryHackMe SOC path! It was a challenging but rewarding experience. The path covered a wide range of topics related to security operations centers, including incident response, threat hunting, and log analysis. I learned a lot about the tools and techniques used by SOC analysts, and I feel much more confident in my ability to work in a SOC environment. The hands-on labs were particularly helpful, as they allowed me to apply what I learned in a practical setting.
I highly recommend this path to anyone interested in cybersecurity, especially those looking to work in a SOC. The content is well-structured and the challenges are engaging. Plus, the community support on TryHackMe is fantastic, making it easy to get help when needed.
The Modules
The path had 8 modules:
Module 1: Cyber Defence Frameworks
This was the easiest and most straightforward module. I got through all 8 rooms in a single day. It was super easy barely an inconvenience.
8 Rooms
Module 2: Cyber Threat Intelligence
After the first module, I kind of went into sleep mode and did nothing for the new few weeks. It was really hard to get myself to return. It took me 24 days to actually start the second module.
This module was a little more interesting but still boring in the grand scheme of things. I learned about the different types of threat intelligence tools and how to use them to gather information about potential threats. I finally learned how to use YARA rules (I’m probably still going to ask ChatGPT to generate them for me). I also learned OpenCTI and MISP! My favorite room from this module was Friday Overtime where I investigated an attack and got to use my OSINT skills.
7 Rooms
Module 3: Network Security and Traffic Analysis
From this point on, I was on a roll. It took me a whole week to finish this module, but I was super consistent and put in the work every single day.
This module had 15 rooms. A lot of new tools and a
Overall, this room was pretty tough since I’m bad a memorizing things. I had to keep looking up commands. I honestly don’t remember most of them now.
15 Rooms
Module 4: Endpoint Security Monitoring
In this module, I discovered that OSQuery is a thing. I had never heard of it before, but it’s a really cool tool for endpoint monitoring. I also learned about Sysmon and how to use it to monitor Windows systems. I have learned Wazuh before but I got to learn more about it in this module. Woo lots of logs!
9 Rooms
Module 5: Security Information and Event Management
Hands down my favorite module. I learned about SIEMs and how they work. I also got to use Splunk for the first time! I had heard a lot about it but never actually used it before. It was really fun to play around with and I learned a lot about how to use it for log analysis.
I also learned about ELK and how to use it for log analysis. I had used ELK before but never really understood how it worked. This module really helped me understand the inner workings of ELK and how to use it effectively.
Itsy Bitsy and Benign were my favorite rooms from this module. They were both really fun and challenging.
9 Rooms
Module 6: Digital Forensics and Incident Response
Another long and honestly boring module. The main thing I learned from this module is that I really don’t like digital forensics. It’s just not my thing. I did learn a lot about the different tools and techniques used in digital forensics, but I don’t think I’ll be using them anytime soon.
15 Rooms
Module 7: Phishing
This module was a lot of fun! I learned about the different types of phishing attacks and how to defend against them. Lots of fishing 🐟🐟
6 Rooms
Capstone
The final 4 rooms were actually really tough. Tempest took me a whole day to complete. Boogeyman 1 and 2 were also really challenging. I had to use all the skills I learned in the previous modules to complete them. It was a great way to wrap up the path and test my knowledge.
The most fun was the final challenge Boogeyman 3. Working with Elastic and Kibana is so much fun! I really enjoyed analyzing the logs and finding the clues to solve the challenge. It was a great way to end the path.
4 Rooms
Final Thoughts
I really enjoyed this whole path. It was a great way to learn about SOC operations and the tools used in the field. I feel much more confident in my ability to work in a SOC environment now. Happy hacking!
Enjoy Reading This Article?
Here are some more articles you might like to read next:
